In today’s world, cloud computing has become a buzzword, and with the proliferation of cloud technology, security has become a major concern. As more and more businesses migrate their infrastructure and workloads to the cloud, it becomes increasingly important to ensure that these resources are secure and protected from external threats.
Microsoft Azure has come up with Azure Bastion, a fully managed platform that provides secure and seamless RDP and SSH access to virtual machines directly through the Azure portal. In this blog post, we will discuss what Azure Bastion is, its benefits, and how to get started with Azure Bastion using a step-by-step demo.
What is Azure Bastion?
Azure Bastion is a fully managed PaaS service that allows you to securely connect to your virtual machines using RDP and SSH directly from the Azure portal. It eliminates the need for a public IP address, VPN connection, or jump server to access your virtual machines. With Azure Bastion, you can access your virtual machines with just one click from the Azure portal, and it provides an additional layer of security by using Azure Active Directory for authentication.
Azure Bastion is a great solution for businesses of all sizes who want to improve the security of their virtual machines and simplify the process of accessing them. By eliminating the need for a public IP address, VPN connection or jump server, Azure Bastion reduces the attack surface area of your virtual machines and provides a more secure way to access them.
Benefits of Azure Bastion
Azure Bastion provides several benefits that improve security and ease of use. Some of the benefits are:
- No Public IP Address Required: One of the main benefits of Azure Bastion is that it does not require a public IP address or inbound port rules, which reduces the attack surface area of your virtual machines. This means that you can keep your virtual machines more secure without having to worry about managing public IP addresses or inbound port rules.
- Secure Access: Azure Bastion provides a secure way to access your virtual machines by using Azure Active Directory for authentication. It eliminates the need for VPN or jump servers, which can be cumbersome to manage and can increase the risk of security breaches. With Azure Bastion, you can rest assured that your virtual machines are secure and protected from external threats.
- Ease of Use: Another benefit of Azure Bastion is that it provides a seamless experience for accessing your virtual machines directly from the Azure portal with just one click. It eliminates the need for multiple tools, such as Remote Desktop or PuTTY, which can be time-consuming and difficult to manage. With Azure Bastion, you can access your virtual machines quickly and easily, without having to worry about managing multiple tools or applications.
Setting up Azure Bastion Service
In this guide, we’ll walk you through the process of setting up Azure Bastion to securely manage your virtual machines (VMs) within a virtual network (VNet) without exposing them to the public internet.
Current Environment Overview
Let’s start by understanding my current setup before we secure our Virtual Machines with Azure Bastion. My current setup consists of:
- Resource Group: All resources are organized within a resource group named
BastionGuide. This helps in managing and maintaining the resources efficiently. - Virtual Network (VNet): A virtual network named
myVNetwith an address space of10.0.0.0/16. This VNet provides a secure, isolated network environment for our resources. - Subnet: Inside the VNet, there is a subnet named
VMSubnetwith an address range of10.0.2.0/24. This subnet houses our virtual machines and provides internal network segmentation for better management. - Network Security Group (NSG): The subnet is secured by an NSG named
vmNSG. NSGs contain rules that allow or deny network traffic to the VMs, ensuring an additional layer of security. - Virtual Machines: We have two virtual machines within the subnet:
myLinuxVM: A Linux VM running Ubuntu 18.04 LTS.myWindowsVM: A Windows VM running Windows 10 Pro (22H2).
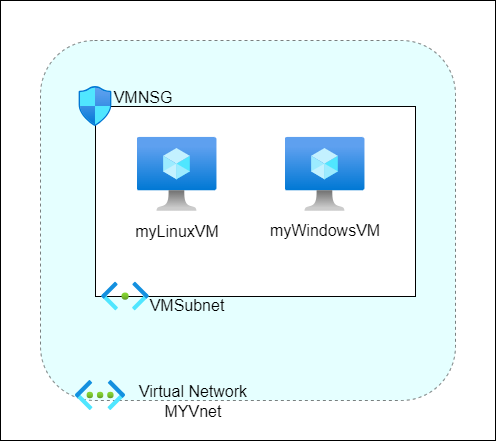
This diagram represents the initial state of my setup as described above.
Creating Azure Bastion Service
Now you will set up Azure Bastion for securely accessing your Virtual Machines in your Virtual Network.
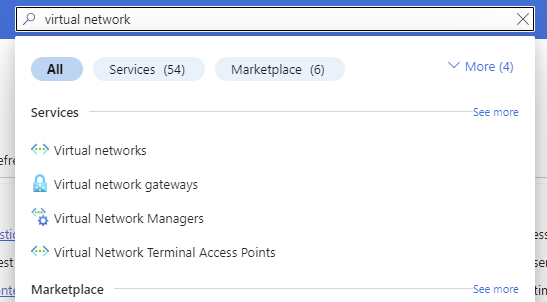
- In the Azure search bar, search for Virtual Networks and select Virtual Networks:
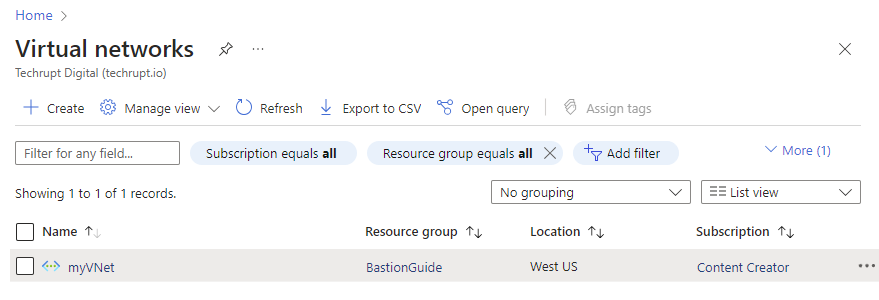
- Choose the Virtual Network where your Virtual Machines are hosted. myVNet is used in this case**:**
 Your will be taken to your Virtual Network’s overview page.
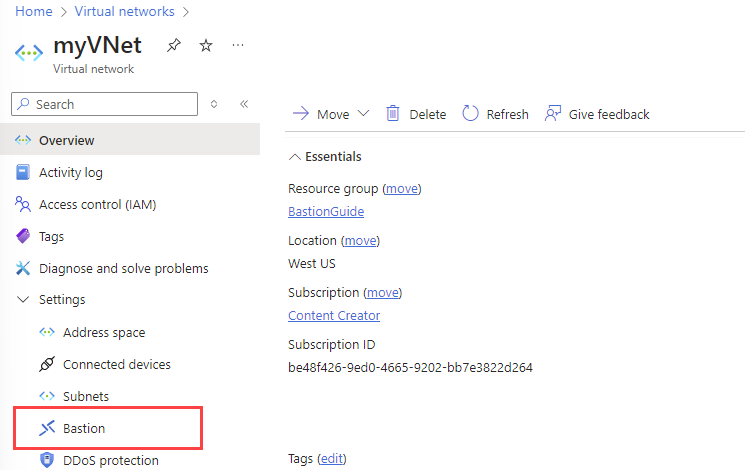
Your will be taken to your Virtual Network’s overview page. - On the Virtual Network’s overview page, under Settings, select Bastion:
- On this page, Fill out the following information and click Connect:
- Select a VM to connect to
- Authentication Type: Select your VM’s authentication type. Mine is VM Password
- Username: Your VM’s username
- Password: Your VM’s password
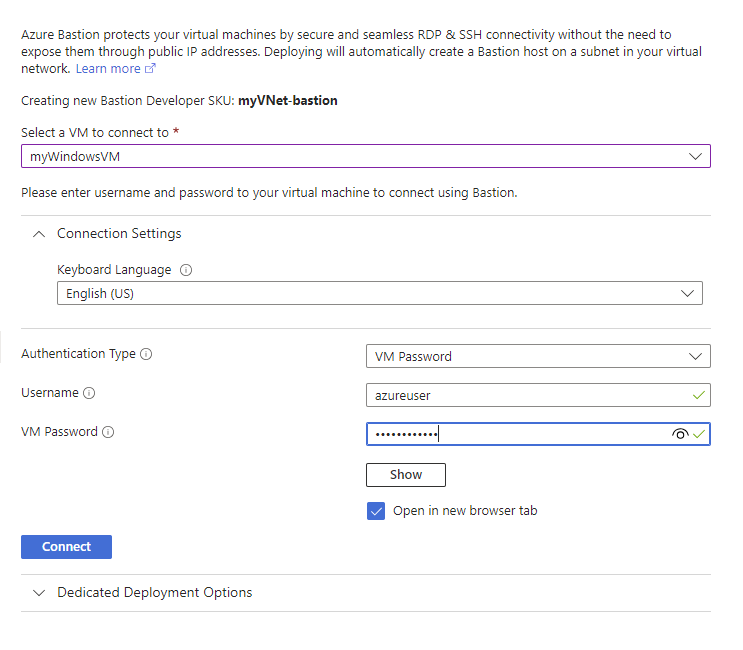
Note: This will create a new Bastion service with the Developer SKU. Azure Bastion offers several SKUs with different features to suit various need. It provides basic functionality, allowing connections to VMs within the same virtual network using RDP and SSH. However, it lacks support for more advanced features such as connecting to peered virtual networks, concurrent connections, and integration with Azure Key Vault.
Depending on your needs, consider using the Basic or Standard SKU. Check our this Bastion SKU comparison table for more information.
Your VM will open in a new tab in your browser.
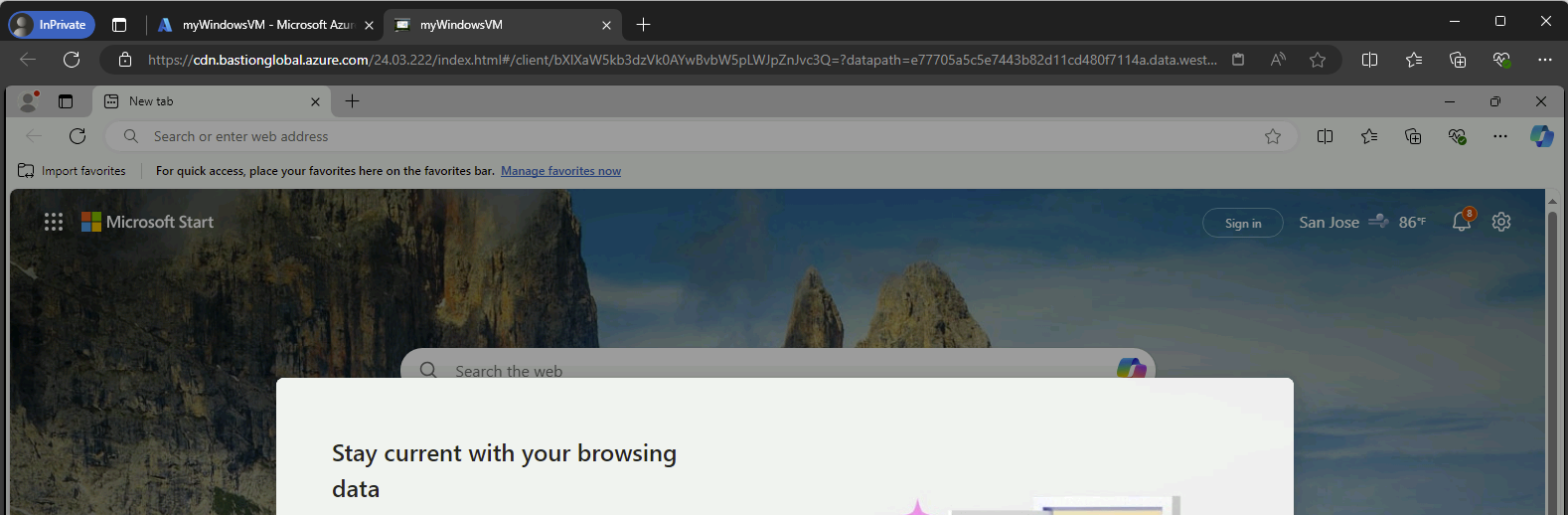
The Bastion service created can now be used to securely connect to all the Virtual Machines in your Virtual Network. Test your Bastion service by connecting to a different VM. In my case, I will connect to my conveniently named myLinuxVM.
Testing Azure Bastion Service
Now that your Bastion service has successfully deployed, test it by using it connect to some of the other VMs in your VNet.
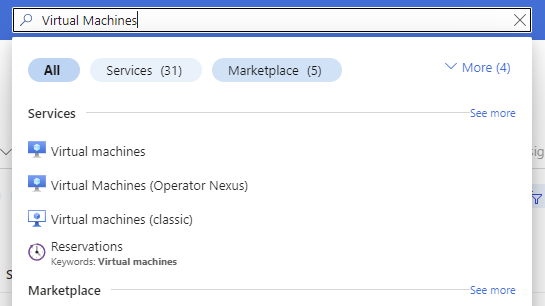
- In the Azure search bar, type Virtual Machines and select Virtual machines:
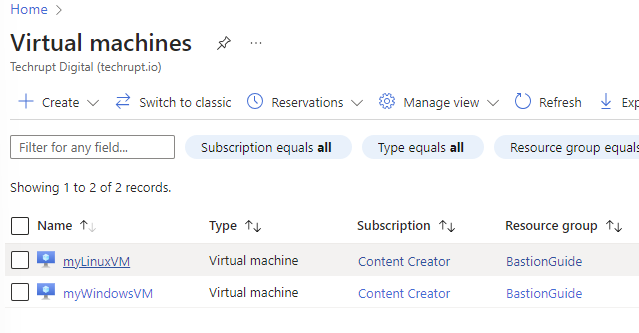
- Select a different VM from the one you used above. In my case, I will select myLinuxVM:
- In the top bar, click on Connect and Connect via Bastion:
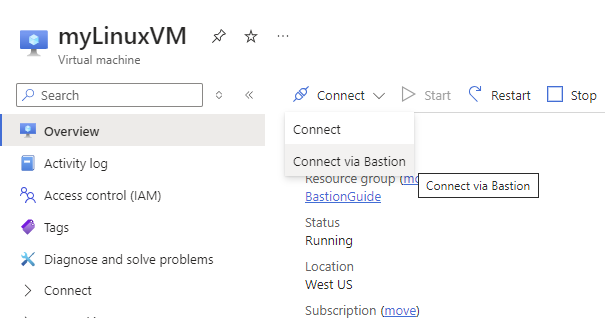 This will take your to the Bastion tab of your VM service.
This will take your to the Bastion tab of your VM service. - On this page, Fill out the following information and click Connect.
- Authentication Type: Select your VM’s authentication type. Mine is VM Password
- Username: Your VM’s username
- Password: Your VM’s password
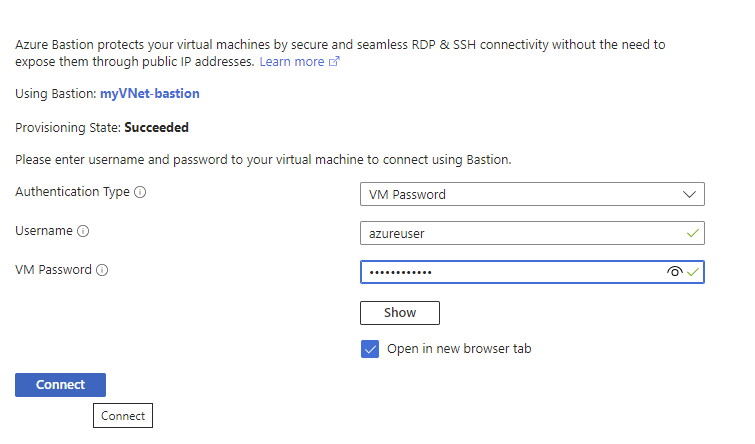
Your VM will open in a new tab in your browser.
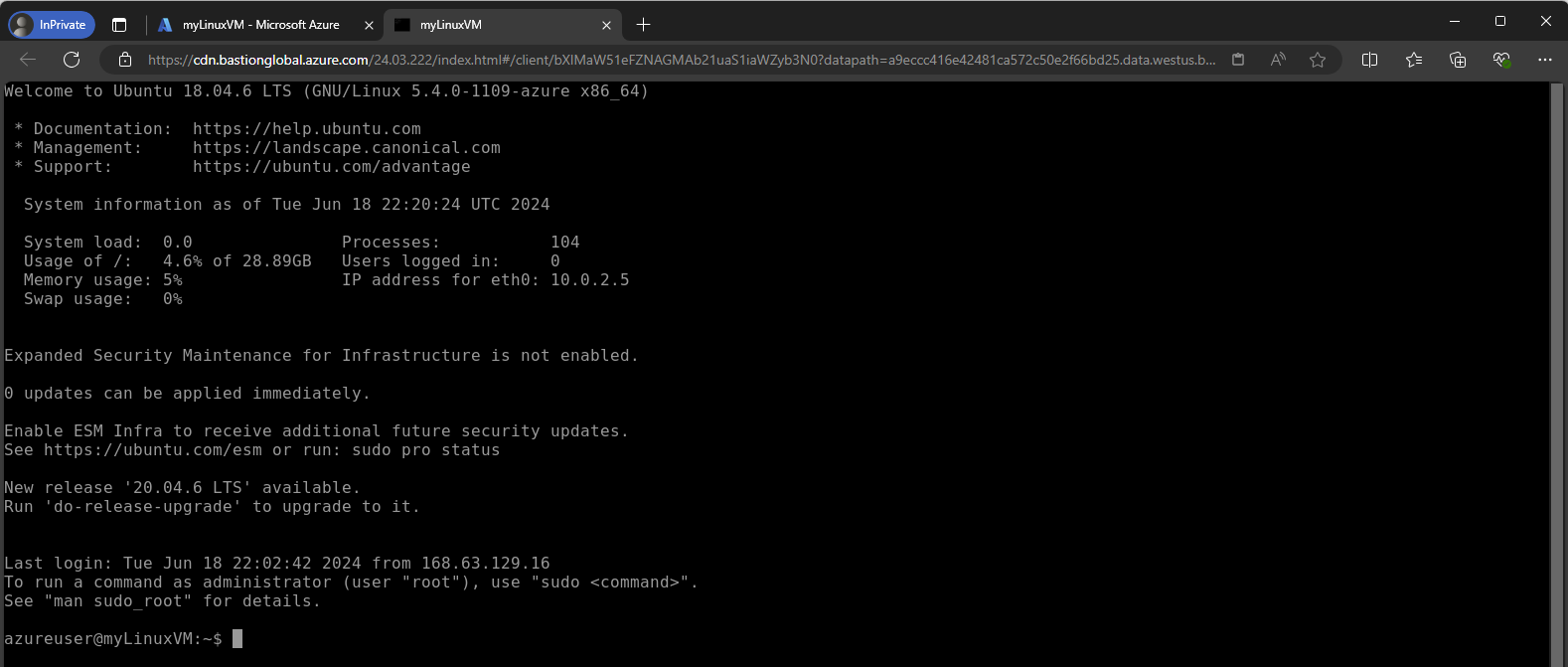
You have successfully created and configured Azure Bastion. Now, you can securely access your virtual machines directly from the Azure portal without exposing them to the public internet.
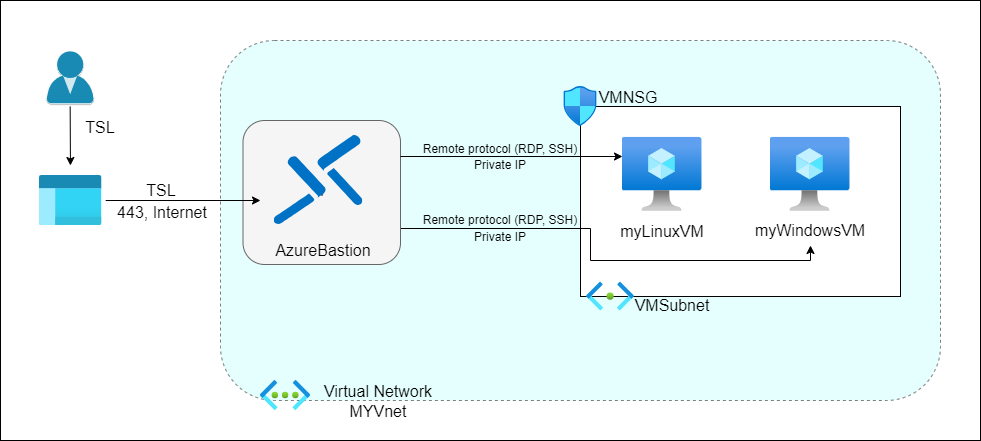
In this updated diagram, users connect to their VMs through Azure Bastion using a secure TLS tunnel, ensuring data security and integrity. The VMs remain within the VMSubnet and are protected by the Network Security Group (vmNSG), with Azure Bastion acting as a secure gateway. This architecture not only improves security but also simplifies the management of remote connections, providing a seamless and safe way to access your virtual machines.
Pricing Comparison
Azure Bastion is priced on an hourly basis, and the costs can vary significantly depending on the SKU chosen. Below is a breakdown of the hourly pricing for each SKU:
- Azure Bastion Developer: Free
- Azure Bastion Basic: $0.19 per hour
- Azure Bastion Standard: $0.29 per hour
- Additional Standard Instance: $0.14 per hour
- Azure Bastion Premium: $0.45 per hour
- Additional Premium Instance: $0.22 per hour
At $0.19 per hour, the Basic SKU can add up to approximately $136.80 per month (calculated as $0.19 * 24 hours * 30 days). the Standard SKU can accumulate to about $208.80 per month (calculated as $0.29 * 24 hours * 30 days). If additional instances are required for scaling, each extra instance costs $0.14 per hour, adding another $100.80 per month per instance. You should consider Automating Bastion deployment using Azure Logic Apps to cut costs.
Security Considerations for Azure Bastion
Azure Bastion comes equipped with several security features designed to keep your virtual machines (VMs) safe:
- No Public IP Addresses: By eliminating the need for public IP addresses, Azure Bastion greatly reduces the risk of attacks. This means your VMs are not directly exposed to the internet, enhancing their security.
- Azure Active Directory Integration: Azure Bastion integrates with Azure Active Directory (AD) to authenticate access to your VMs. This added layer of security ensures that only authorized users can connect to your VMs, leveraging the robust security features of Azure AD.
- Fully Managed Service: As a fully managed service, Azure Bastion is continuously maintained and updated by Microsoft. This means you benefit from the latest security patches and updates without having to manage them yourself, keeping your infrastructure secure and up-to-date.
Common Use Cases for Azure Bastion
Azure Bastion is especially useful in various scenarios where security and ease of access are paramount:
- Secure Remote Access: Azure Bastion provides a secure way to connect to your VMs using RDP and SSH without exposing them to the public internet. This is perfect for accessing your servers remotely while keeping them secure.
- Testing and Development: For developers and testers, Azure Bastion offers a secure access point to their development and testing environments in the cloud. It simplifies access management and ensures these environments remain protected.
- Enterprise Environments: In large-scale enterprise settings, Azure Bastion helps centralize and secure access to numerous VMs. It reduces the attack surface by eliminating public IP addresses and integrates with Azure AD for secure authentication, making it an ideal solution for complex and extensive cloud infrastructures.
Conclusion
Azure Bastion is a secure and easy-to-use platform that provides seamless RDP and SSH access to virtual machines directly from the Azure portal. It eliminates the need for a public IP address, VPN connection, or jump server, which reduces the attack surface area of your virtual machines. With Azure Bastion, you can improve the security of your virtual machines and simplify the process of accessing them. Whether you’re a small business or a large enterprise, Azure Bastion is a great solution for securing your virtual machines and improving the overall security of your cloud infrastructure.
Discover more from Parveen Singh
Subscribe to get the latest posts sent to your email.





